Why Governments Centralize IT Security
Recognizing the need to hire its first chief information security officer, Cook County, Ill., brought in Ricardo Lafosse in May 2013 to consolidate and oversee its disparate security systems. He was delighted with the challenge.
Shortly after joining Cook County, Lafosse set the ambitious goal of creating an open, collaborative security environment for all 11 county agencies. "This was no easy task," he says. "Efforts at this scale had never been attempted for information security."
The plan was to create a security framework that addressed each agency's unique security requirements and provided a minimum baseline for those agencies to implement. The solution would improve the security posture of Cook County as a whole and ensure that each department had the support and tools needed to achieve the baseline.
Renee Murphy, senior analyst of security and risk management for Forrester Research, agrees that centralizing IT security across departments or agencies brings several benefits. "It ensures they're purchasing with economies of scale, aligns the needs of stakeholders, and funds the security projects that reduce the greatest amount of risk," she says. "By collaborating across agencies, facilities can reduce costs through operational efficiencies."
Creating a Unified Approach
"The first order of business was to assess the situation and identify areas that could quickly benefit from security technologies," says Lafosse. Cook County implemented malware detection and prevention software at all egress points to catch any weaknesses missed by the collection of decentralized point products.
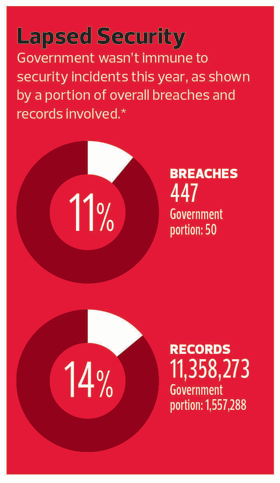
Percentage of public-sector data breaches that occurred as a result of miscellaneous error*
SOURCE: Verizon, "Data Breach Investigations Report," 2014
Lafosse's team set out to collaborate with other agencies. Some agency IT workers had limited exposure to security resources, while others were more advanced. To establish credibility, Lafosse's department showed its expertise in areas such as updating policies and responding to incidents.
"We had to be inclusive and demonstrate the advantages of not going it alone," he says. In addition to convincing agency IT staffs of the benefits of an integrated security solution, the security team assured departments they'd be able to retain some degree of autonomy. Once everyone was on board and agency concerns were addressed, Cook County officials and IT leadership came together to draft and pass an information security ordinance.
The next order of business was to deploy robust endpoint security on workstations in order to report and track security metrics. "The biggest obstacle was finding a single technology that would support various security tools under one dashboard," Lafosse says. Cook County ultimately selected a McAfee unified security architecture. "The platform is robust enough to allow non-McAfee products to share and update information through the McAfee architecture," he says.
Cook County deployed a McAfee security solution that includes the company's VirusScan Enterprise, Host Intrusion Prevention, ePolicy Orchestrator and Enterprise Security Manager, among other security tools.
Centralizing Cook County's information security with McAfee products enables the administrators to share expertise and information to prevent and remediate attacks. What's more, working with a single security vendor simplifies procurement and enables the county to obtain more competitive pricing.
Nevada's Enterprisewide Solution
The state of Nevada's decision in 2013 to centralize critical portions of its information security program was driven by necessity. The number of attempts to compromise state data have climbed steadily from the 2013 benchmark of 1 million per day. More important, the attacks are increasingly more sophisticated.
State IT is highly decentralized, and Nevada's ongoing budget crisis exacerbates the challenge. However, during the 2012 budget discussions, it was clear that the most effective and efficient strategy for the state was to purchase an enterprisewide solution.
"We determined back then that we needed to get the most bang for the buck," says Nevada CIO David Gustafson. "But the only way was to consolidate key security initiatives across the entire executive branch."
Gustafson proposed and later deployed an enterprise Symantec security platform, which included Altirus for the central workstation management platform and Arellia for endpoint protection and application whitelisting. Additionally, the Symantec Web Gateway showed immediate value by detecting and blocking malware downloads to the state. "Nevada needed a state-of-the-art solution that would be familiar to the IT staffs of individual agencies," he says. "It had to play well with others so we could augment the Symantec solution with complementary products from other suppliers," he says.
After the South Carolina Department of Revenue suffered a major breach in late 2012, Nevada's governor directed the CIO to design, procure and implement a statewide information security program. The budget office appropriated the funds that agencies had designated for their individual IT budgets for an enterprise solution, and legislators approved the plan.
"An integrated Symantec solution would provide increased functionality and protection at a very reasonable, incremental cost over what agencies had initially budgeted for anti-virus software alone," Gustafson says.
The Benefits of Centralizing Security
In Ada County, Idaho, a centralized security environment creates a solid, countywide security posture that reduces overhead and provides consistency.
Bret Lopeman, cybersecurity officer for Ada County, says the county has relied on Check Point Software Technologies products for 18 years. "We consolidated all products that we felt were 'as good as' or 'better' solutions from Check Point, especially in terms of perimeter security of inbound and outbound traffic," he says.
Ada County uses Check Point 12000- and 4800-series appliances with firewall, virtual private network, intrusion prevention, application control, URL filtering and identity awareness software blades. It supplements Check Point's security capabilities with other products such as McAfee cloud-based email protection, Sophos Endpoint protection, MobileIron mobile device management and IBM QRadar security information and event management.
With multiple products in place, Lopeman says it was difficult to correlate and define exactly what was transpiring on Ada County's network, precisely where to look, and which product to investigate. That increased the support overhead. Consolidating on the single Check Point Next Generation Firewall platform sped response times to customers. "While not a single pane of glass for our overall security platform, it's now a much smaller number of windows to peer into," he says.









